Microsegmentation in the modern Data Center
-
Traditional edge protection practices in a data center with perimeter firewalls, Intrusion Prevention Systems, malware detections are no longer effective in the real world. Breaches do occur and then the attack just continues to expand within the data center.
Data Centers need to employ more granular or segmented policies to thwart the attack from spreading inside the Data center. It is important for network and security teams to strategize micro-segments based on the unique requirements of the applications and the organization itself. In this concept, rules and policies are assigned to workloads, VMs, or network connections. There are many vendors like VMware, Cisco and Juniper who offer Network Virtualization solutions.
With microsegmentation, IT teams assign security policy at the workload level, and that security can persist even when the workload moves across cloud domains. It has now become very important for every organization to have full insight into all of the assets and their interdependencies to build that micro-segmentation plan.
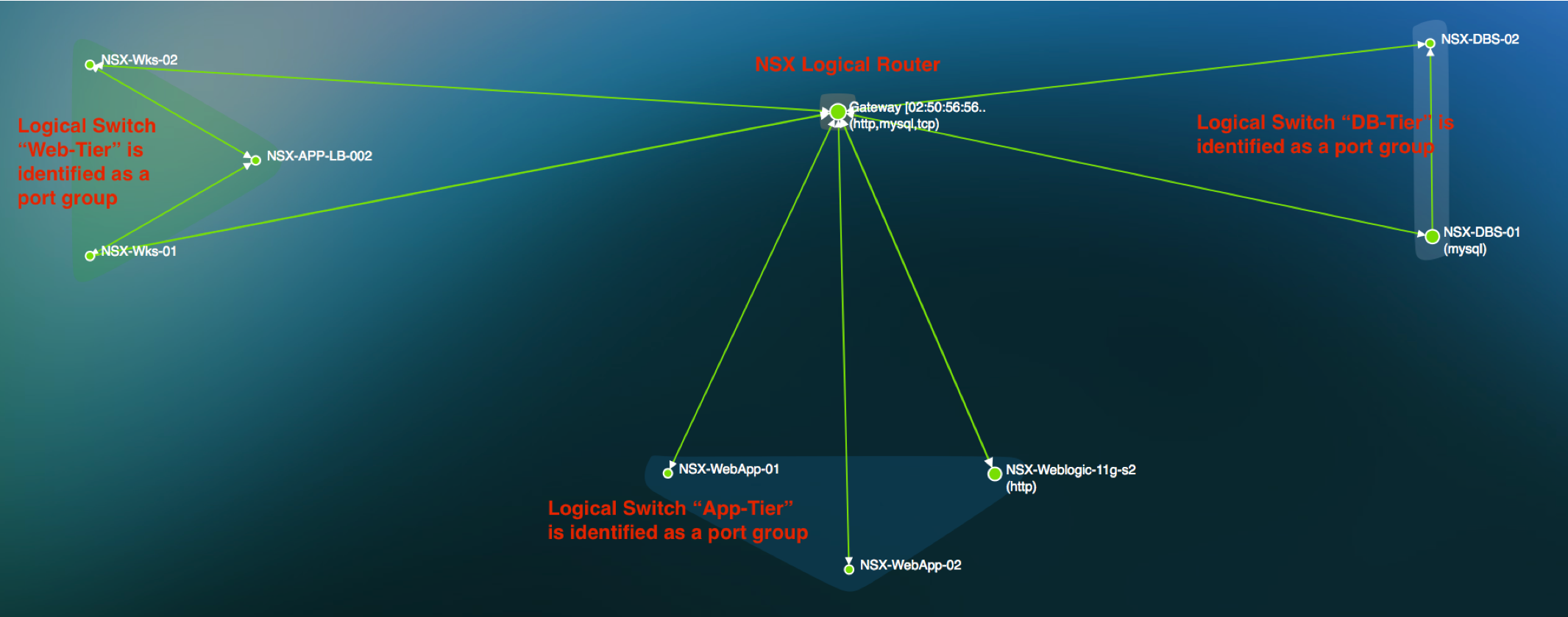
Visualize Interdependencies to build your Microsegmentation plan for VMware NSX and other vendors
- Reduced Time to Value with automatic discovery of the topology map for your microsegmented environment.
- Troubleshoot issues proactively at lightning speeds with full visibility into the dependencies. View each application service performance by its response time and transaction load on the associated VMs.
- No manual updates or interventions needed to build the Dependency mapping. Install Uila, and we will build the maps automatically with NO code changes needed.
- Key Performance Indicators such as Application Response Time, Transaction Volume, packets, etc. for every application discovered.
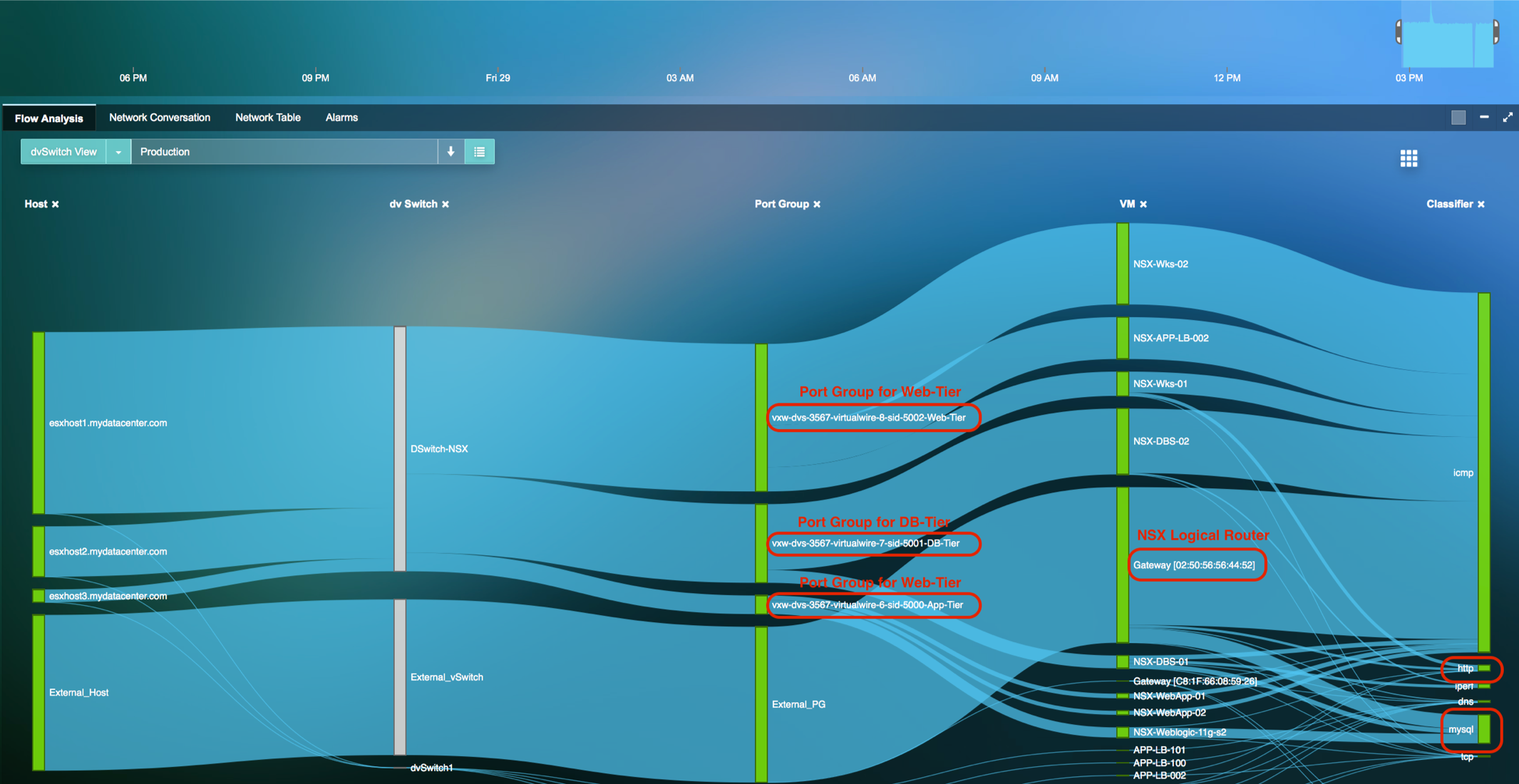
Visualize Network Traffic Flow in a Microsegmented environment
- Visualize how virtual network traffic traverses across physical devices, virtual entities & Application Services, to pinpoint network hot spots impacting application performance.
- Review Network Round Trip Time, Traffic Volume, Retries, Packet Drops, Application Response Time for each application.
- Top-down visualization approach from the Application or Business Service to its correlated Infrastructure and Network root cause for faster root cause resolution.
Monitor East-West Traffic for Microsegmentation Planning & Security Analytics
- Real-time Full Network Security Insight with comprehensive Applications, Network and Infrastructure & East-West traffic statistics across VMs.
- Detect East-West traffic patterns to assist in Microsegmentation Planning. .
- Detect East-West traffic which may indicate that a malware penetrated the outer security perimeter and has launched further attacks inside a vulnerable data center.
- Detect Abnormal patterns of connections and traffic flow indicating a network security threat that could impact business service performance and operations
- Packet Capture for Deep Packet Inspection & Forensic Evidence to solve network security challenges
Resources
-
Blog: Microsegmentation and its PrerequisiteIn this blog, dcdummy.com talks about micro-segmentation and how tools can help
-
Network Security Analytics with UilaQuick product video on how to use Uila for Network Security Analytics.
-
Network Performance Monitoring with UilaQuick product video on how to use Uila for Network Performance Monitoring
-
Application Dependency Mapping with UilaQuick video on how you can Discover & Document Application & Server Dependencies with Uila.
Ready to begin your Monitoring Journey with Uila
Start a 21-day Free Trial Now
Request Trial


 (2).png)



