The Changing Threat Landscape
-
Most enterprise organizations rely on legacy security monitoring practices, that include perimeter security and endpoint protection. But threats these days bypass traditional monitoring solutions and sneak inside the Data Center or the Cloud deployment.
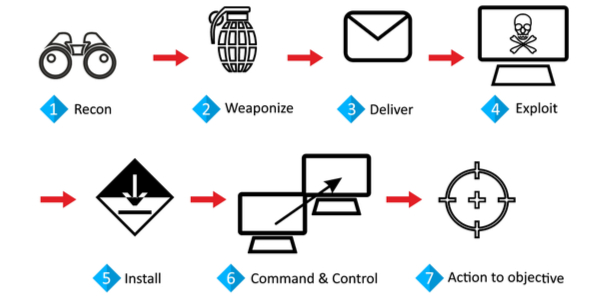
The Threat Landscape in this day and age has also evolved dramatically from the
traditional "grab and dash" as well as mass "spray and pray" exploitation
practices to more sophisticated and patient attacks that impact business
operations for any enterprise organization like never before.
The attacker after breaching the north-south traffic perimeter, conducts internal reconnaissance, gains access to the outside world using Command and Control and then executes its objective which could include stealing of valuable data or bringing down a mission critical service in a stealth manner by moving laterally within the Data Center. This makes lateral or east-west traffic monitoring for any Hybrid Enterprise, the most critical area that needs to be monitored.
Also security teams have limited resources and may not own the right tools that give them the visibility, thus limiting their contribution. This challenges the heavy investement the organization may have already made in the IT infrastructure and security.
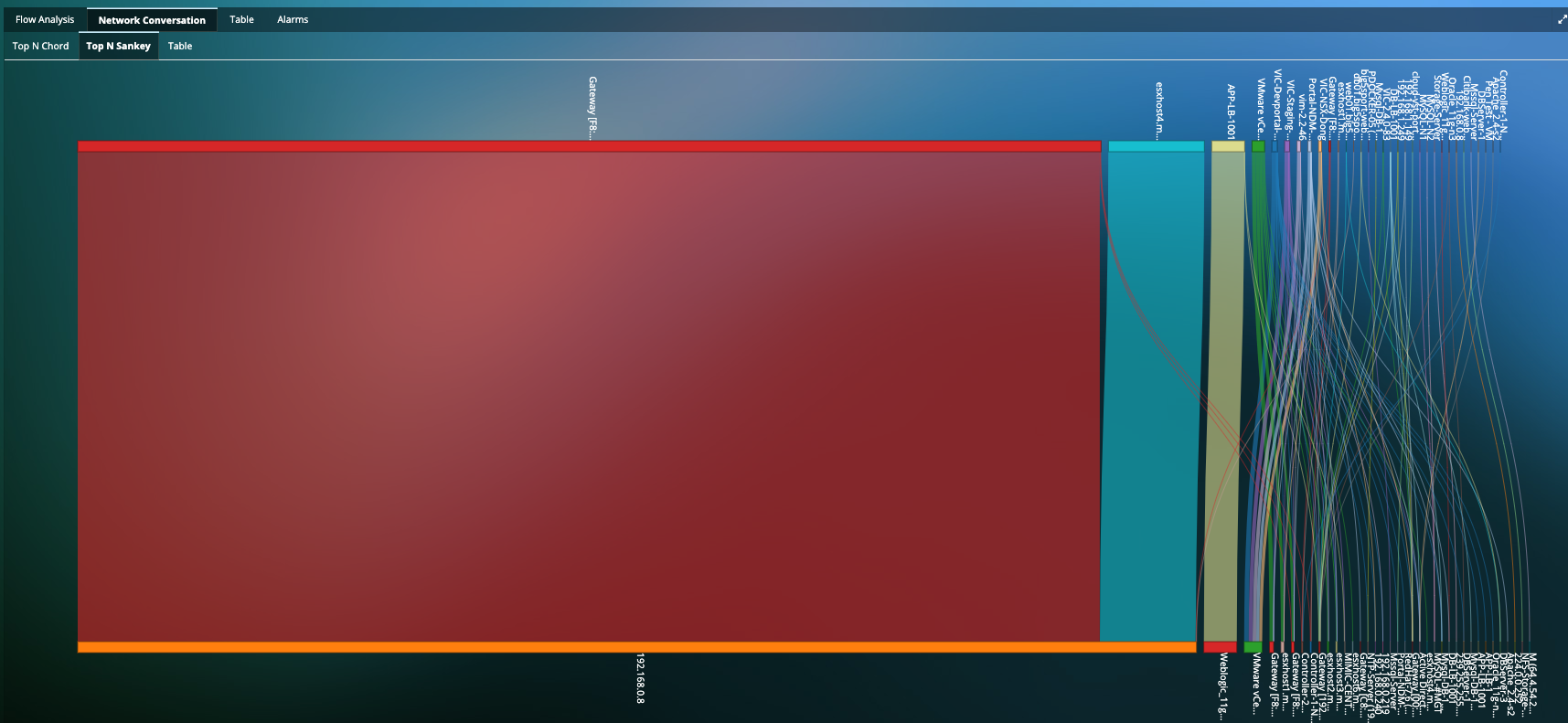
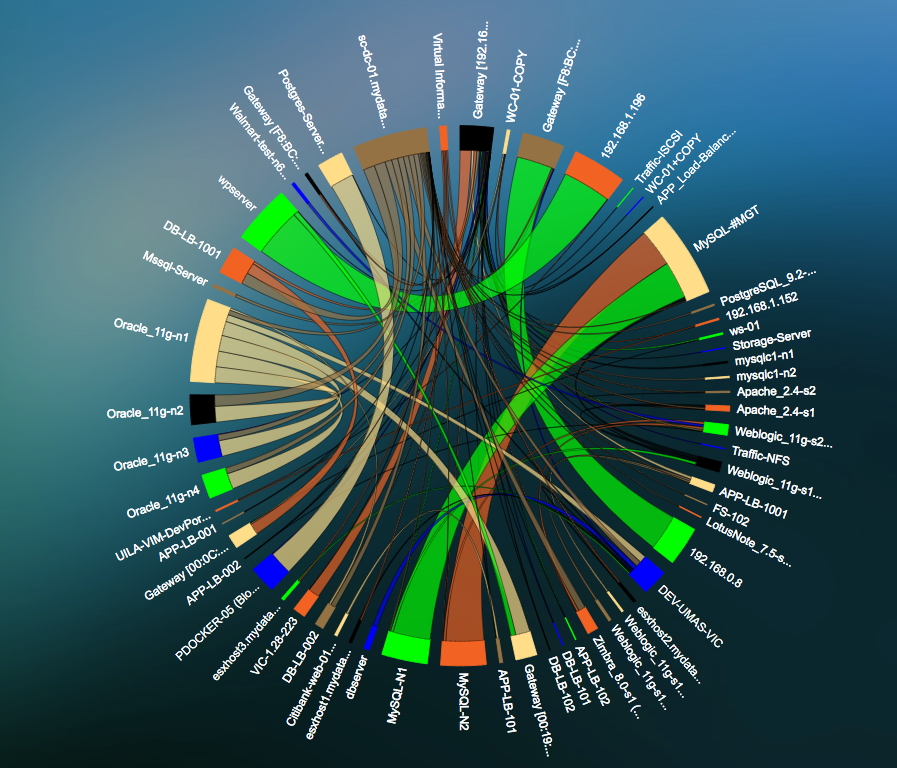
Monitor Lateral Movement of Authorized and Unauthorized Traffic
- Deep visualization of a clear indicator of a threat that is attempting to extend its reach into the network.
- Monitor attackers pivoting between compromised hosts to bounce deeper into the network.
- Network Traffic Insights into Network Traffic, Network Response Time, Fatal retries, Resets, Zero Window, etc.
- Application-centric visualization for traffic between servers to provide insight into applications being compromised, or used to compromise.
Leverage existing Network Packet Broker (NPB) Infrastructure and Investment
- Leverage your existing Network Packet Broker (Niagara Networks, Ixia, etc.) infrastructure and investment by forwarding network traffic from the NPB to Uila's Virtual Smart Taps.
- Add much needed visibility for Application Performance based on Deep Packet Inspection of the network traffic.
- Combine north-south and east-west traffic in a single network traffic analysis view. Get full access to KPIs such as bandwidth, transaction volume, drops, retries, etc.
- Troubleshoot network issues proactively at lightning speeds with full visibility and bottleneck detection across the full-stack and all infrastructure dependencies. Uila's dependency maps are generated automatically, and without any agent deployment.
Click here for more details on Uila's Integration with Niagara Networks
Uila-Niagara Networks Integration
Resources
-
Cyber Threat Monitoring for the Hybrid EnterpriseQuick 3 minute video that talks about the changing Threat Landscape with attacks moving laterally within the Data Center and Cloud deployments, the importance of identifying Application Anomalous Behavior and Data exfiltration activities and finally on how you can protect your mission critical application workloads with Uila.
-
Uila's DPI Methods for Detecting Lateral MovementQuick overview on Uila's DPI methods for lateral movement detection.
-
Lateral Traffic Movement Analysis with UilaQuick video on how Uila can monitor authorized and unauthorized lateral movement or east-west traffic movements within your deployment.
-
Uila for Cyber Threat Monitoring Solution BriefQuick solution brief on Uila's Application-centric approach to cyber threat monitoring.
Ready to begin your Monitoring Journey with Uila?
Start a 21-day Free Trial Now
Request Trial