Automated Asset, Application Inventory and Connectivity Management
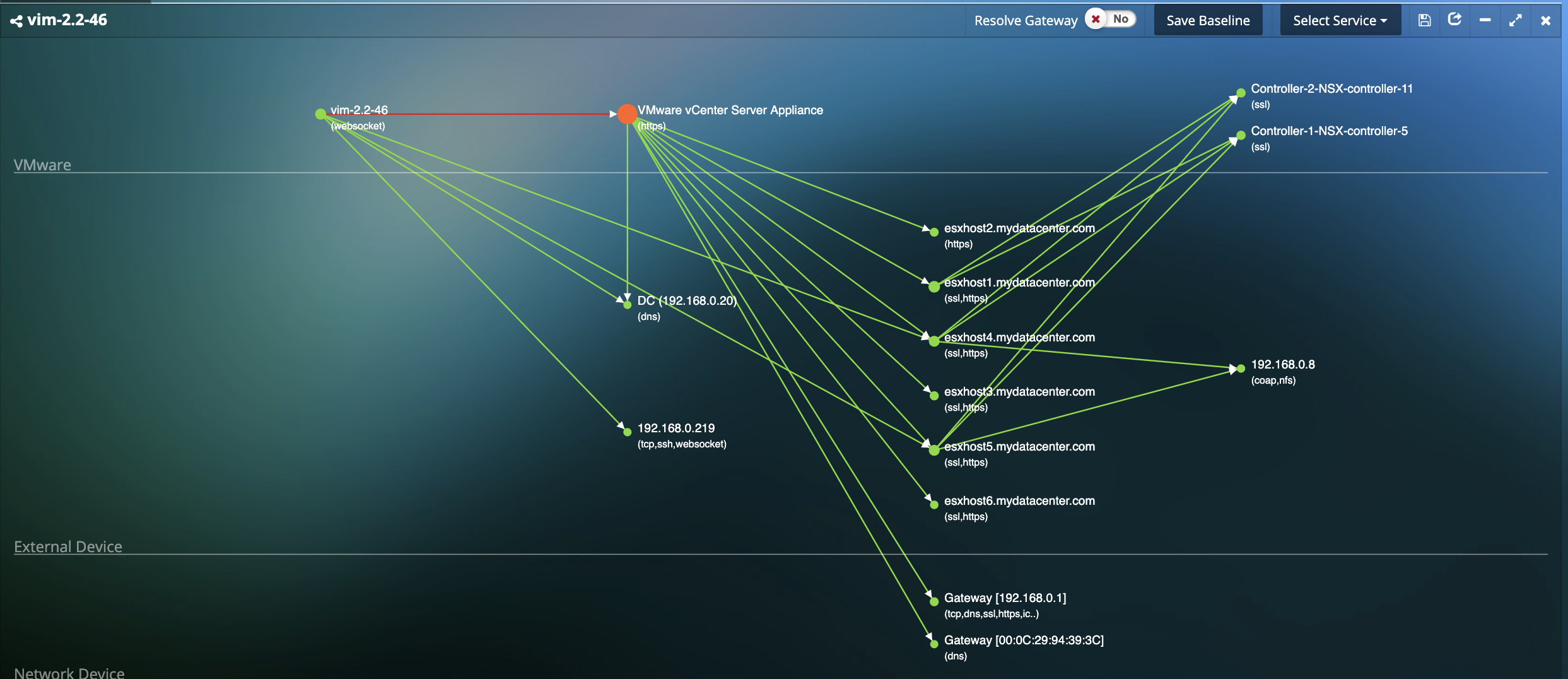
- Automated visualization of all virtual, physical and cloud assets and their interdependencies at the application level without the installation of any agents.
- Direct DPI-based classification for over 3,700 applications (Web, Database, SaaS, Healthcare, Financial, IoT, Building Automation, Industrial, etc.).
- Automatically generated and updated in real-time for all applications.
- Create and customize multi-tier application groups based on your requirements.
Automate SecOps with Intelligent Remediations
- AIOps to streamline any application anomalous behavior (new VMs, new dependencies, unapproved transactions, etc.) and reduce MTTR with remediation actions across the infrastructure. Intelligent Alert-based triggers and Manual triggers provide complete control in proactively preventing issues as well as streamlining problem resolution.
- Increase Security IT team efficiency and agility by automating repetitive tasks and focusings on issues that matter by reducing alert noise.
- Based on Uila’s full-stack ML-based Root-cause analysis that rapidly isolates issues. Actions include Power off VMs, Suspend VMs, Reset VMs, Power On VMs, logging off VDI users, Updating VMware tools, Restart Guest OS, Kill a process running on a VDI desktop, etc.
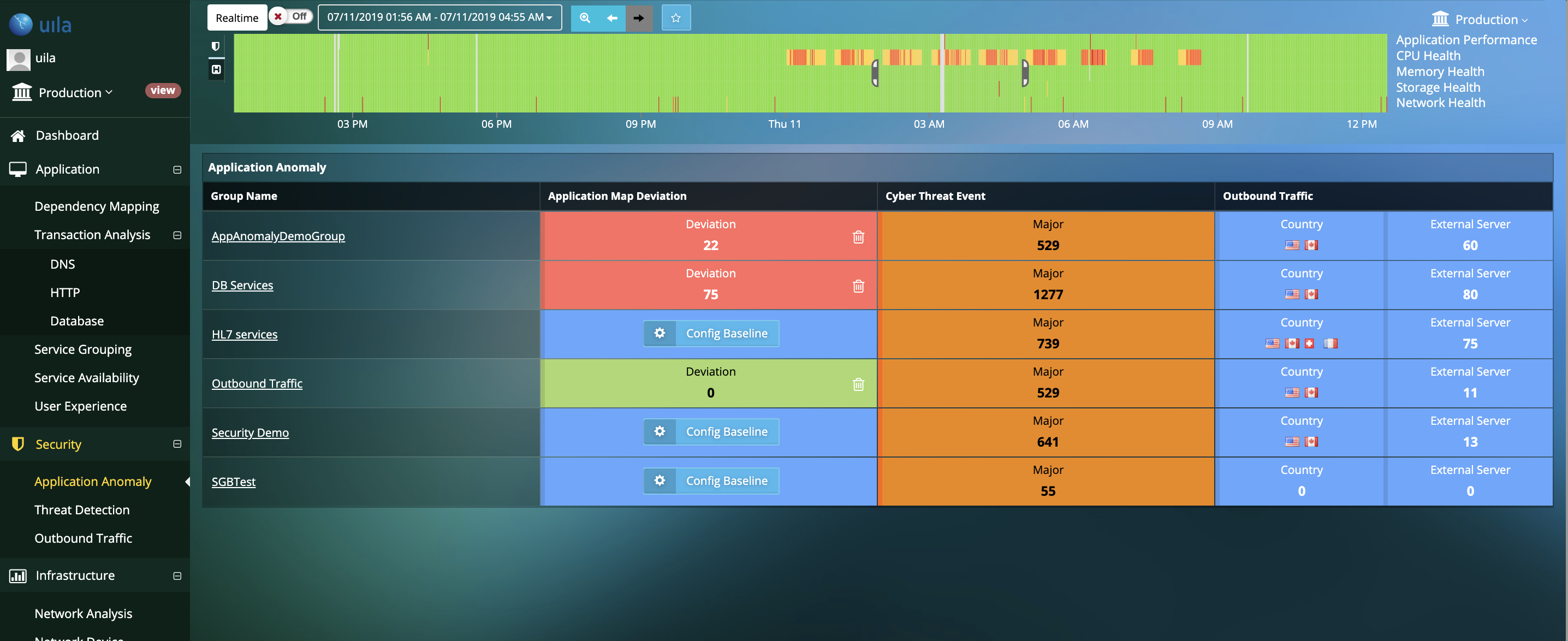
Visualize Application Deviation from Corporate Security Policy
- Identify anomalies in application behavior that may occur before, during or as a follow up after a successful attack
- Insights into deviations such as unauthorized dependency changes, new applications/services/protocols running on the VMs, additions of unauthorized VMs or tearing down of your mission critical VMs, and others.
- Map thousands of cyber threats directly to the anomalous behavior in application performance and dependencies to identify root-cause.
Total Visibility & Control of your Infrastructure for Contingency Planning & Disaster Recovery
- Application auto-discovery for over 3,700 applications with deep packet inspection to identify and avoid unauthorized application rollouts.
- Total visibility into your Infrastructure (Storage, Network, Users, Hosts, etc.) and know what “normal” looks like, to rapidly identify unwanted and unauthorized changes.
Resources
-
Cyber Threat Monitoring for the Hybrid EnterpriseQuick 3 minute video that talks about the changing Threat Landscape with attacks moving laterally within the Data Center and Cloud deployments, the importance of identifying Application Anomalous Behavior and Data exfiltration activities and finally on how you can protect your mission critical application workloads with Uila.
-
Application Behavior Anomaly Detection with UilaQuick video on how Uila can identify anomalies in application behavior that may occur before, during or as a follow up after a successful attack.
-
Uila for Cyber Threat Monitoring Solution BriefQuick solution brief on Uila's Application-centric approach to cyber threat monitoring.
-
Security Analytics and Change Control in the Modern Data Center White PaperRead this white paper to get insights into the security and change control issues of the Modern Data Center.
-
Shadow IT challenge? Take back controlIn this blog we talk about Shadow IT and how organizations can take back control of their own environment and destiny.
-
Wine Producer Success StoryUila Success Story on how a large wine producer solved their Shadow IT challenges.
Ready to begin your Monitoring Journey with Uila?
Start a 21-day Free Trial Now
Request Trial