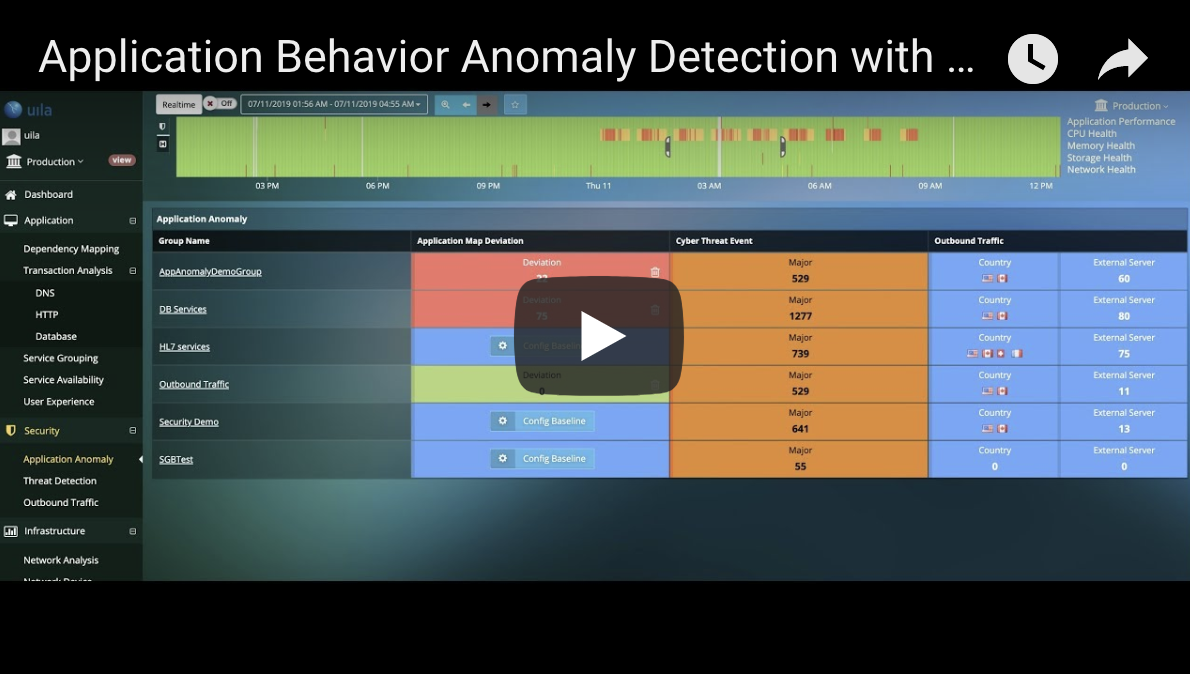
Visualize Application Behavior Deviation from Corporate Security Policy
- Identify anomalies in application behavior that may occur before, during or as a follow up after a successful attack
- Insights into deviations such as unauthorized dependency changes, new applications/services/protocols running on the VMs, additions of unauthorized VMs or tearing down of your mission critical VMs, and others.
- Map thousands of cyber threats directly to the anomalous behavior in application performance and dependencies to identify root-cause.
- Get alerted automatically to application behavior deviations.
Read More
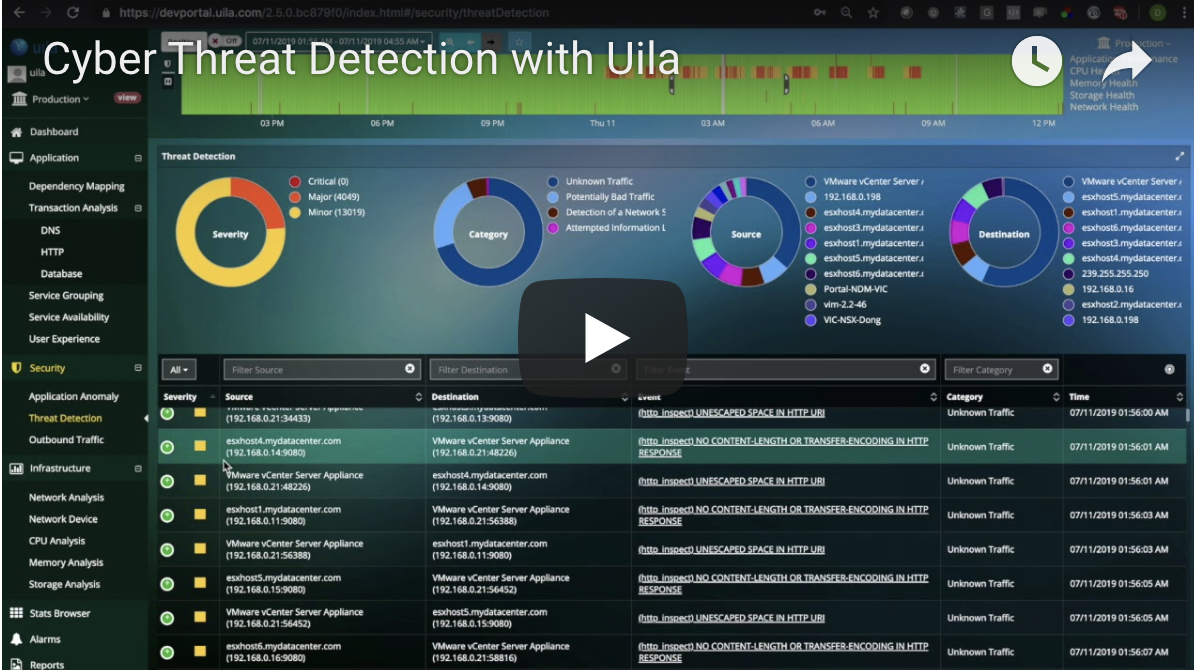
Proactively Detect Advanced Malicious & Evasive Threats in Real-Time for Data Center and Cloud Workloads
- Real-time Detection for thousands of Advanced and Persistent threats including Malware, Exploit Kits, Webshells, Port Scans, SMB Probes, Obfuscation, OS fingerprinting, etc.
- Deep Infrastructure & Application Insights into Current as well as Potential Compromised Assets.
- Reduce Risk associated with outbound connections with immediate visibility into Traffic Exfiltration from your deployment to unauthorized or malicious locations directly on a world map.
- Prioritize your efforts with visibility into the Top Exploited Hosts.
Read More
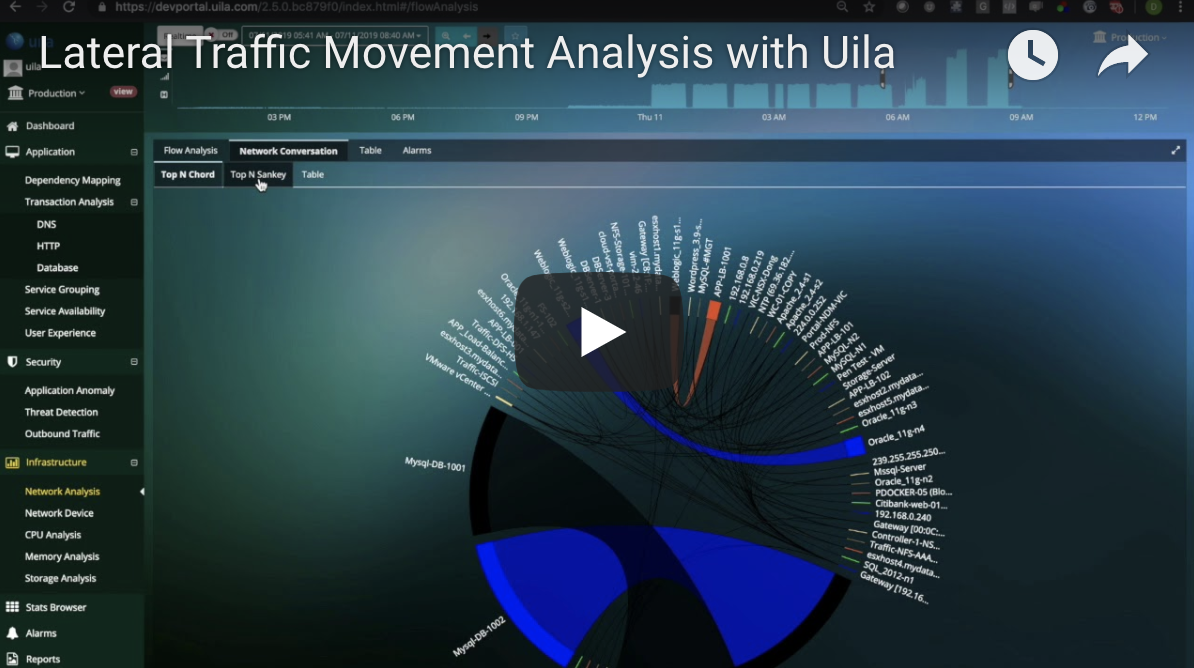
Monitor Lateral Movement of Authorized and Unauthorized Traffic
- Deep visualization of a clear indicator of a threat that is attempting to extend its reach into the network.
- Monitor attackers pivoting between compromised hosts to bounce deeper into the network.
- Network Traffic Insights into Network Traffic, Network Response Time, Fatal retries, Resets, Zero Window, etc.
- Export network traffic results for forensic evidence.
Read More
Resources
-
Identifying TLS 1.0Quick video that talks about TLS 1.0 and how Observability solutions can be used to identify systems running this outdates and insecure protocol.
-
Cyber Threat Detection Landscape and Detection with UilaLearn about cyber threats impacting Data Center deployments.
-
Uila's DPI Methods for Detecting Lateral MovementQuick overview on Uila's DPI methods for lateral movement detection.
-
Uila for Cyber Threat Monitoring Solution BriefQuick solution brief on Uila's Application-centric approach to cyber threat monitoring.
-
Security Analytics and Change Control in the Modern Data Center White PaperRead this white paper to get insights into the security and change control issues of the Modern Data Center.
-
Data Center Security ChallengesIn this blog, we talk about the four critical security challenges IT teams face in any data center.
-
Shadow IT challenge? Take back controlIn this blog we talk about Shadow IT and how organizations can take back control of their own environment and destiny.
-
Wine Producer Success StoryUila Success Story on how a large wine producer solved their Shadow IT challenges.
Ready to begin your Cyber Threat Protection Journey with Uila
Start a 21-day Free Trial Now
Request Trial