In today's increasingly complex IT environments, understanding how applications interact with each other is crucial for maintaining performance, security, and scalability. Application Dependency Mapping (ADM) plays a vital role in this process by identifying and visualizing the relationships between different applications within a network. One of the most effective techniques for ADM is Deep Packet Inspection (DPI). This blog delves into the importance of DPI-based Application Dependency Mapping and how it can revolutionize network management.
What is Deep Packet Inspection (DPI)?
Deep Packet Inspection is a form of network traffic filtering that examines the data part and the header of a packet as it passes through an inspection point. DPI can be used to identify applications, protocols, and services, providing a more granular view of network traffic.
Why Application Dependency Mapping Matters
Application Dependency Mapping involves identifying and documenting the interactions between applications, servers, and services within an IT infrastructure. It is crucial for:
- Application Classification: DPI provides the application classification, while the ADM will provide the crucial information on how the applications are dependent on each other, and hotspots leading to poor application performance.
- Improved Network Visibility: ADM provides a clear picture of how applications communicate with each other, making it easier to identify potential bottlenecks, vulnerabilities, or misconfigurations.
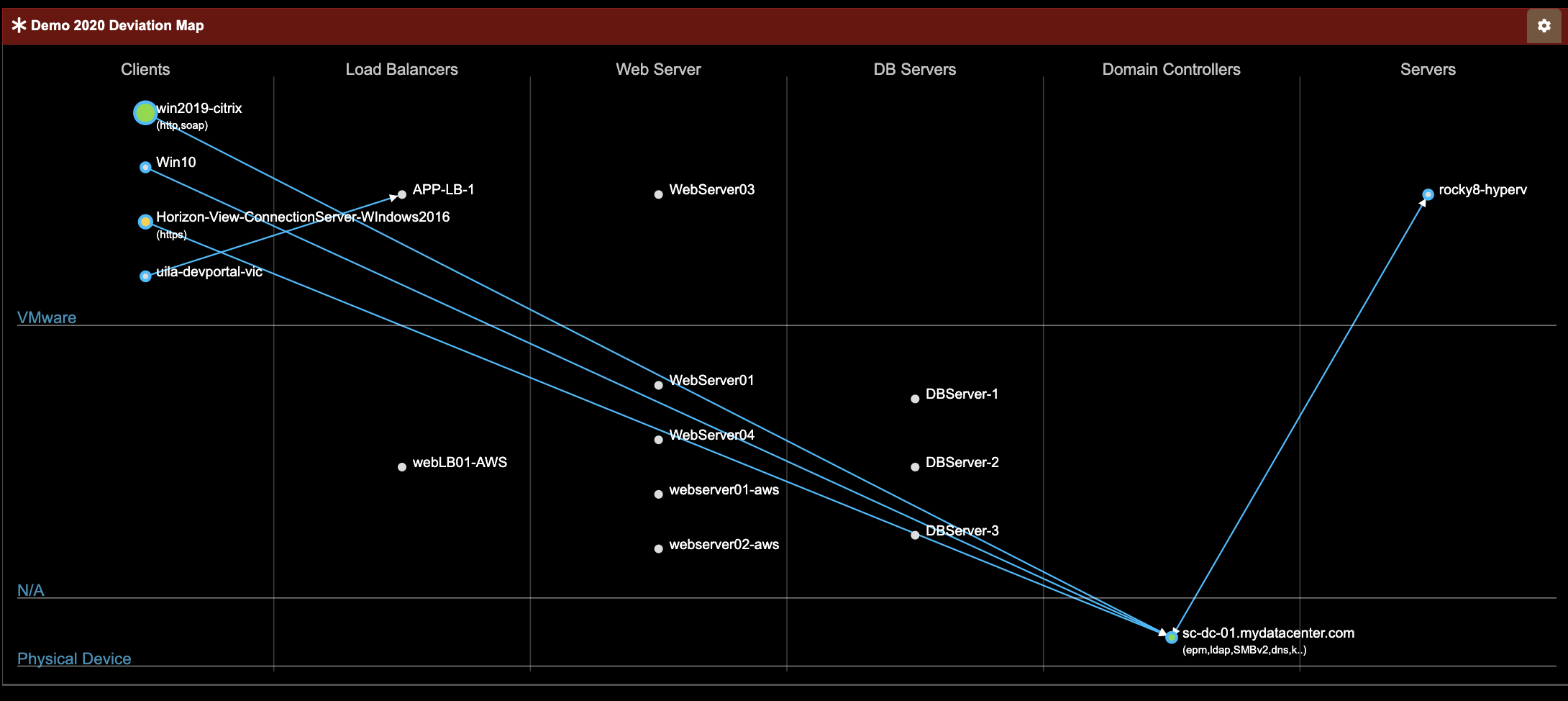
- Enhanced Security: By understanding application dependencies, organizations can better protect critical assets, enforce security policies, and quickly identify and mitigate threats. Here is an example of how Uila uObserve identifies application anomalous behavior in the environment. This includes addition, deletion or modification of any dependencies, that could indicate a cyber threat issue.
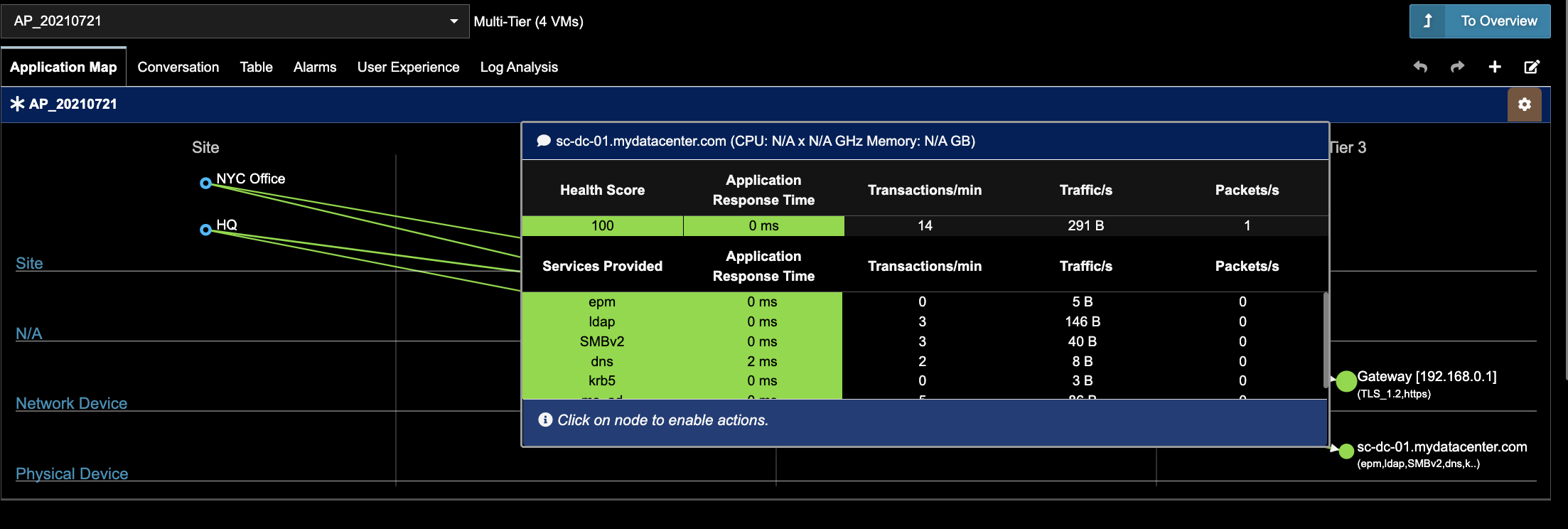
- Efficient Troubleshooting: When an issue arises, ADM helps quickly pinpoint the root cause by showing the interdependencies between different components, reducing downtime and improving Mean Time to Resolution (MTTR). Here is an example of how Uila uObserve can help you drill down to performance challenges.
- Optimal Resource Allocation: Understanding how applications interact enables more efficient resource allocation, ensuring that critical applications have the necessary bandwidth and resources to function optimally.
The Role of Deep Packet Inspection in ADM
DPI enhances Application Dependency Mapping by providing detailed insights into network traffic. Here’s how DPI contributes to a more effective ADM process:
1. Granular Traffic Analysis
DPI can identify the specific applications and services involved in communication by analyzing the payload of data packets. This granular level of detail is essential for accurately mapping dependencies, especially in environments where multiple applications use the same protocols or ports.
2. Real-Time Observability
DPI allows for real-time monitoring of network traffic, enabling organizations to track application dependencies as they evolve. This is particularly important in dynamic environments where new applications and services are frequently introduced.
3. Protocol and Application Classification
DPI can recognize a wide range of protocols and applications, even those that use encryption or non-standard ports. This capability ensures that all dependencies are identified, providing a comprehensive view of the network.
4. Security and Compliance
By inspecting the contents of packets, DPI can detect malicious traffic, unauthorized applications, and non-compliant application/network behavior. This is critical for maintaining the security and integrity of the network, especially in regulated industries.
5. Enhanced Troubleshooting
DPI’s detailed analysis can help quickly identify and diagnose issues within the network. For instance, if a specific application is experiencing performance issues, DPI can reveal whether the problem lies within the application itself or its dependencies.
Use Cases of DPI-Based ADM
1. Data Center Migrations
During data center migrations, it’s essential to understand the dependencies between applications to ensure a smooth transition. DPI-based ADM provides the necessary insights to plan and execute migrations with minimal disruption.
2. Cloud Migrations
Moving applications to the cloud requires a clear understanding of their dependencies. DPI can help identify which applications are suitable for migration and which ones may require additional resources or adjustments.
3. Security Audits
Regular security audits are necessary for maintaining compliance and protecting sensitive data. DPI-based ADM provides the detailed information needed to identify and address potential vulnerabilities within the network.
Conclusion
Deep Packet Inspection plays a crucial role in Application Dependency Mapping by providing detailed insights into network and application-specific traffic. As environments become more complex and dynamic, the importance of understanding application dependencies cannot be overstated.
By integrating DPI into your ADM processes, you can ensure that your network is secure, efficient, and ready to meet the demands of today’s digital landscape.
Subscribe
Latest Posts
- How Data Center System Administrators Are Evolving in today's world
- Microsoft NTLM: Tips for Discontinuation
- Understanding the Importance of Deep Packet Inspection in Application Dependency Mapping
- Polyfill.io supply chain attack: Detection & Protection
- Importance of Remote End-User Experience Monitoring
- Application and Infrastructure Challenges for Utility Companies
- Troubleshooting Exchange Server Issues in Data Centers
- Importance of Application Dependency Mapping for IT Asset Inventory Control
- Navigating the Flow: Understanding East-West Network Traffic
- The imperative of full-stack observability




